Cyber Polygon
International online training for raising global cyber resilience
The teams take on the role of a blue team to investigate an incident using classical computer forensics techniques and the threat hunting approach
Cyber Polygon 2024 results
Cyber Polygon 2024
This year, the training took place online on BI.ZONE Cyber Polygon Platform and within MENA ISC in Saudi Arabia.
In the 24 hours of the training, participants from all over the world practiced repelling a sophisticated targeted attack and further investigated the incident using classical forensics and threat hunting techniques






309 teams from 65 countries
took part in the training
BI.ZONE
Cyber Polygon Platform
Cyber Polygon Platform
This is an online cyber fitness center for training the skills and assessing the potential needed to protect against cyber threats. The scenario from the 2024 training is already uploaded to the platform and is available to individual users
Go to platform


Plot
A well-known startup develops an innovative solution powered by AI. The release of the product is a success, and the company signs multimillion dollar contracts
Company management begins to suspect that the developments were stolen through a breach of the internal infrastructure
The AI model starts degrading. At the same time, a competitor announces the development of a similar product, but at a lower price. All this can lead to a collapse of the company
While intellectual property experts examine the competitor’s solution, the company invites a team of forensic specialists, which the participants are a part of
The teams investigated possible leaks and a compromise of the internal infrastructure

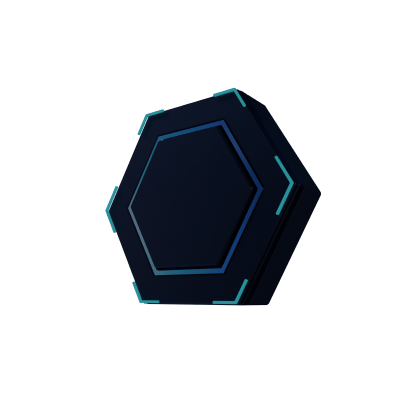
Company infrastructure
Users&AD
The company’s staff segment. This is the largest segment and most vulnerable to attackers.
Many employees are not able to deal with cybersecurity threats. This weak point is often exploited by attackers
R&D Dev
This segment is a sandbox and research lab.
In this segment, researchers and developers invent, implement, and improve new product features, as well as test new ideas, develop prototypes, and test how different components work together
DataLake
This segment contains huge data arrays which are used to train the ML model. The arrays can be both raw and customized.
The DataLake segment is a kind of information storage for the data used in model training. The scope and quality of this data largely determine the ML model performance
R&D Prod
This segment is dedicated to creating release versions of the application or application updates. From here, the application is sent to repositories for further distribution to end users.
Once in this segment, attackers can inject malware into the release versions of the product, disrupt production, or simply steal the source code before it is compiled and secured for distribution
IT
This segment is the heart of the company and the foundation of its business. This is where all its products are created. It is a space for developers, testers, DevOps specialists, and all those directly involved in the creation and development of products.
By infiltrating this segment, attackers can quietly steal the company’s know-how or destroy the business altogether
Admin
A segment that is supervised by administrators who manage corporate information assets.
Administrators have more authority than other employees. Therefore, the admin segment is a valuable assets for the company and an appealing target for intruders
Internet
No business can operate without an Internet connection. This includes Internet access for employees, email communication, file sharing, and messengers.
The global network is also widely used by threat actors. Therefore, any external connections need to be monitored more closely than internal network communications. First and foremost, protection is ensured for the corporate perimeter
DMZ
A segment that hosts corporate public-facing services, such as websites or external file storage. Since these services most often interact with the outside environment, they are logically separated from the private infrastructure.
Security controls in this segment are stronger than in the company’s main protected perimeter
Subscribe for updates
Experts about Cyber Polygon

Organizer

BI.ZONE is an expert in digital risks management that helps organizations develop their business safely in cyberspace